My Experience Passing the OSWE Cert
After some months, I finally decided to share my experience with the AWAE course and how I passed the OSWE cert on the first try.
Every now and then I get DMed on linkedin asking about this exam. Hopefully this will help me redirect people to this blog every time I get asked again, get some organic traffic, monetize with google ads, throw it into sh*tcoins, and eventually retire to a remote japanese village. 🍜⛩️
spoiler: there will be no spoilers here. It’s just my personal experience without anything that isn’t already public.
os-what?
The Offensive Security Web Expert (OSWE) from OffSec is probably the most advanced web penetration testing cert along with the Certified Web Exploitation Expert (CWEE) from HackTheBox.
WEB-300: Advanced Web Attacks and Exploitation (AWAE) is the course behind the OSWE certification and covers a wide range of web exploitation skills and techniques, including:
- analyzing and exploiting a deserialization remote code execution (RCE) vulnerability in the DotNetNuke (DNN) platform
- mastering advanced web security methodologies such as fuzzing, static and dynamic analysis, and manual code review
- practicing session hijacking techniques to gain unauthorized access to sensitive data and functionality, including exploiting an RCE vulnerability in the Dolibarr application using a dedicated virtual machine
Let me stress that it is a white-box penetration testing course, meaning you should must review the source code to find vulnerabilities, but also to a dynamic instance so you can validate them. You need to excel at both. Plus, you have to write an exploit that automates the whole process.
reqs
From my experience, these skills matter:
- dynamic black-box testing: web pentesting, bug bounty, or CTF background.
- secure code reviews: knowing what a vulnerability looks like from the code perspective. In my case, having worked on tuning SAST tools helped a lot.
- scripting: you ultimately need to create working exploits in your language of choice.
- development: not required to know how to build full apps in every language, but it definitely helps.
pre-prep
Before buying any course I like to do my own research and prepare notes based on the official syllabus and real people’s experiences.
It’s also a nice excuse to polish my osint skillz, lol. And to make it more challenging I try to stick to free resources.
I split my research into two buckets:
- general vibe
- official OffSec docs
- Medium articles and personal blogs to get a sense of how people approached it
- Reddit boards like r/oswe or r/codereview
- books related to the topic
- topic specific: I go through the course content and for each topic I search for:
- articles explaining the concepts
- relevant tools
- YouTube videos
- CTFs
- sample exploits from Exploit-DB
- instances of that vuln in different languages (java, C#, python, js, etc.)
prep
Once I felt comfortable with the topics, I bought the AWAE course. My strategy:
- read the huge course PDF1. Thoroughly, underlining the important stuff.
- do the course labs and some of the extra miles
- complement the course with extra research and CTFs
- create my own notes and exploits
Overall, I liked how the AWAE course was structured. You learn by pwning throught specific case studies. It doesn’t dump the solution on you but shows the thought process step by step. Something doesn’t work, then it explains why and how to break it.
This approach works because you see everything in context, and that helps you to develop a good intuition.
notes
I used Notion for notetaking2 and started categorizing vulns like below, but it ended up quite messy3:
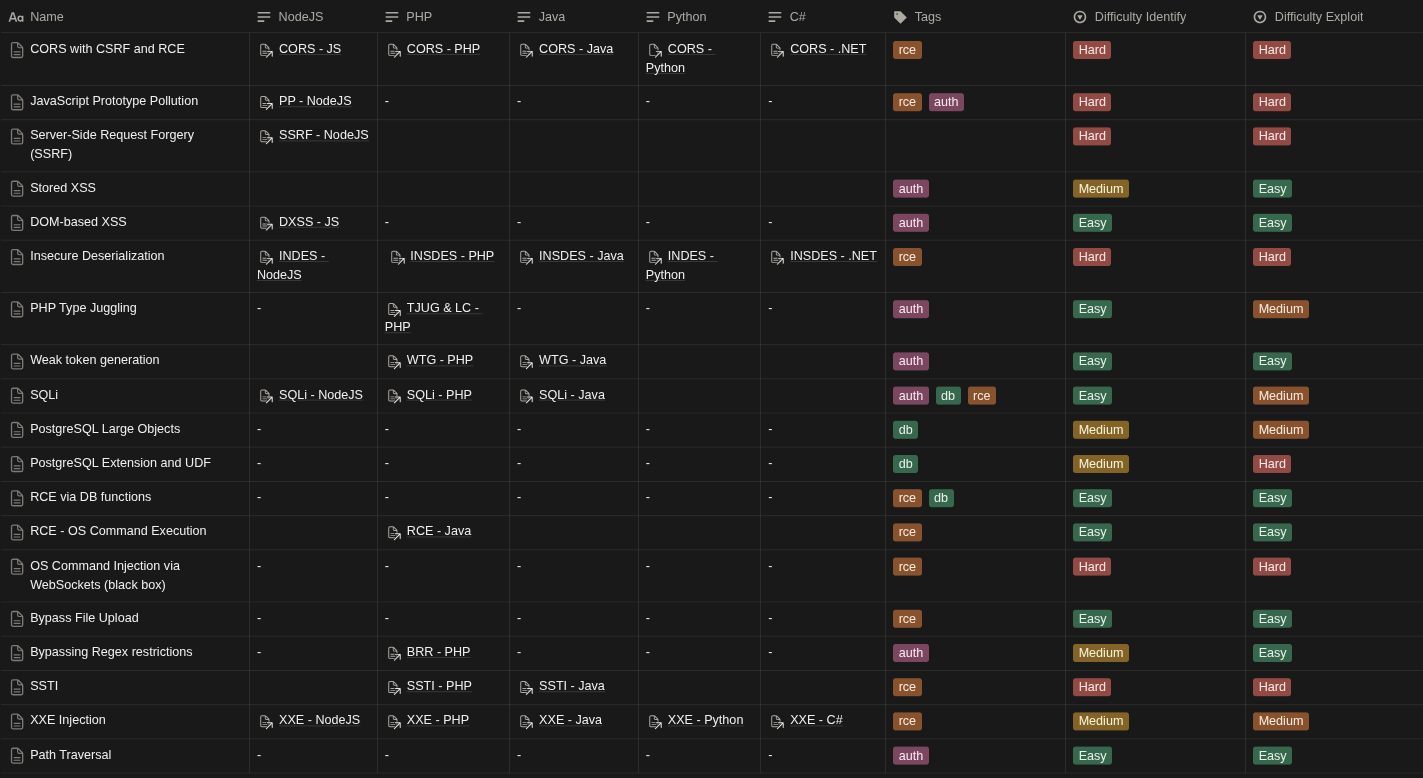
So I created what I called the Exploit Zoo🦒4, basically a collection of payloads and exploits for each topic, neatly categorized and tagged:
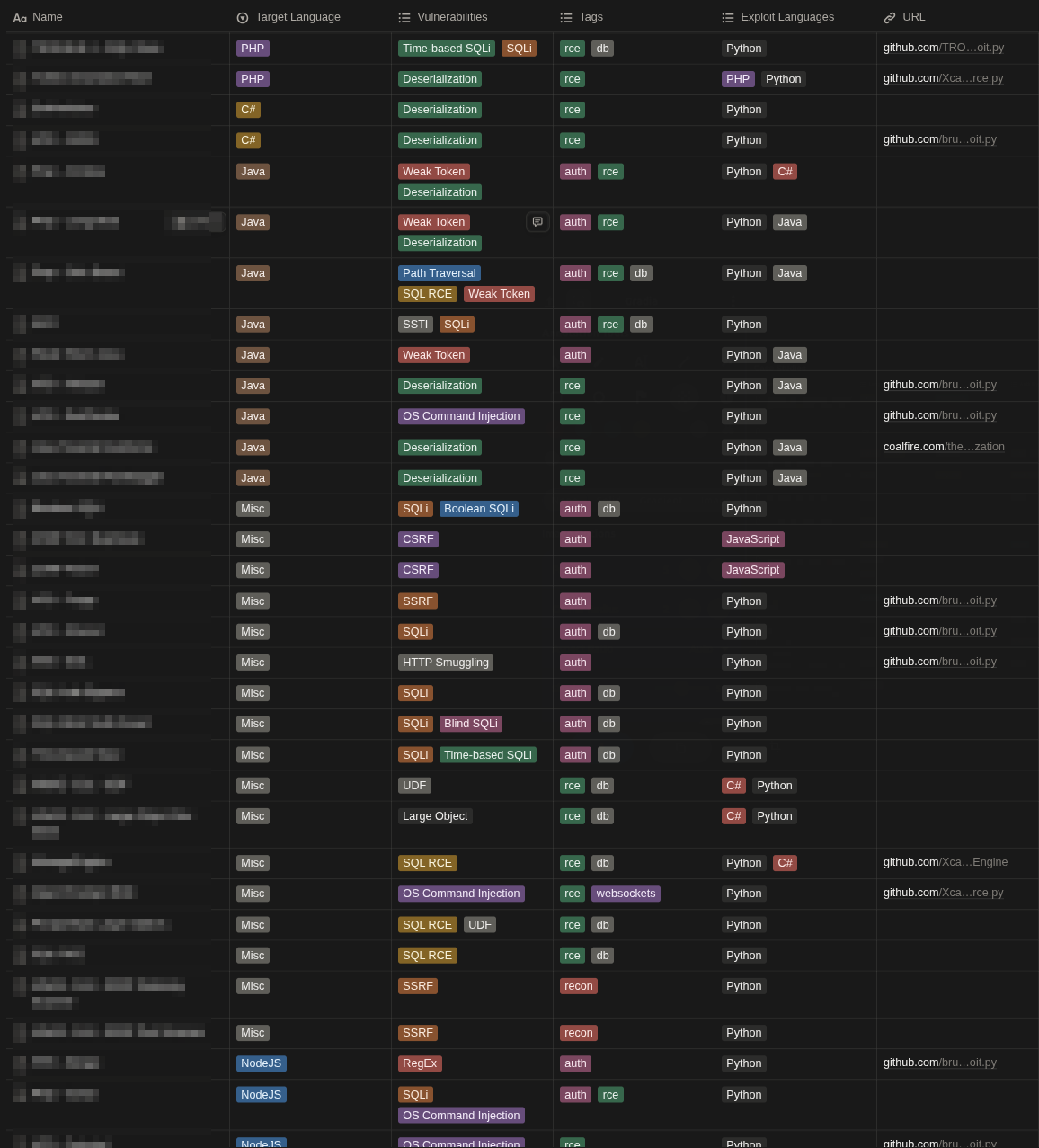
I also organized the writeups of each lab with the working code like this:
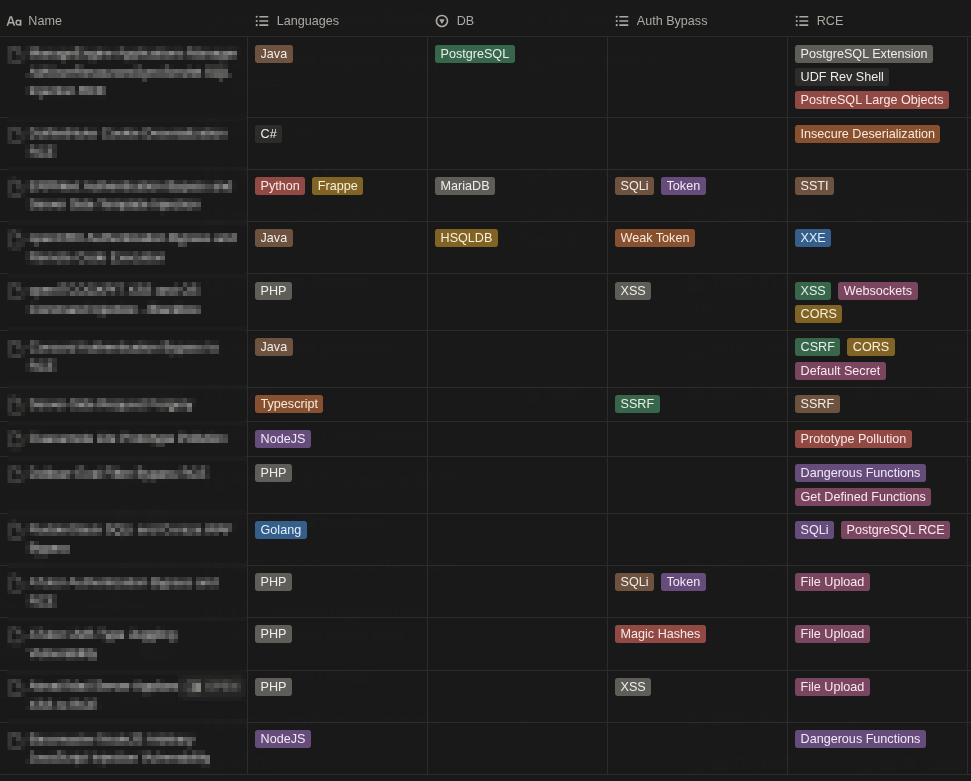
Sure, I know you can code everything from scratch during the exam, but having a solid starting point saves you precious minutes when the clock is ticking.
exam
After almost three months in the course, I decided to take the exam. You get 48 hours to break into two machines and 24 hours to write the report.
I kicked it off early in the morning. The onboarding was painless, the proctoring experience was smooth, and the environment behaved decently.
The first hours went well and I landed an admin bypass. I took a walk to cool off. A few hours later I popped RCE and felt like a god.
Then I got humbled stuck for a while, so I had no option but to listen to some metal and go full Michael Burry mode. 🤘
The real problem was me skimming the exam description and missing a key detail. Once I caught that, I tested my idea dynamically and it worked. After that it was just building the exploit.
TBH, the whole thing was tougher than I expected. Slept three hours, skipped lunch, cried harder, pushed through, and finally grabbed the flag in the last hour.
Next day I cleaned up the notes, sorted the screenshots, and wrote the report following the required format. Used the default OffSec DOCX template this time, but I’ll probably switch to SysReptor in the future.
tips
- pwn all labs including extra miles
- prepare exploits for each vuln type beforehand
- develop your own methodology, you need a plan
- know how to debug, if not you are cooked
- read the exam instructions carefully
- seriously, read the freaking exam instructions
resources
Here is a non-exhaustive list of resources I found useful throughout the journey:
CTFs:
github repos:
- oswe specific:
- other:
- absoluteappsec/handouts: IMO, these guys have the best E2E secure code review methodology out there. Also found here. Pure gold.
- brutuspt/0click_HTB
- elqal3awii/WebSecurity-Academy-with-Python
- VoorivexTeam/white-box-challenges
misc:
- Youtube - @TJ_Null’s OSWE Prep
- OWASP_Code_Review_Guide_v2.pdf
- WSTG - Stable OWASP Foundation
- HTB and Vulnhub: An OSWE Approach
- IppSec writeups
additional tools:
wh00t wh00t
Fast forward two days, I got the email from OffSec telling me I passed. 🎉

The big takeaway, and IMHO what separates a junior from a senior web pentester, is the ability to chain vulns. 🔗
To do that you need to understand the vulnerability in depth: what it is, why it happens, how to exploit it, what possibilities it opens, whether there’s another vuln you can combine to maximize impact, and so on.
As a friend of mine likes to say 5:
you cannot avoid lose your time, without having lost your time in the past
Meaning that only by practicing you develop a sense of what is productive and what is not. In this exam, you will have tons of ideas, but there are plenty of possibilities (and rabbit holes), and you won’t have time to validate every hypotesis that comes to mind. You have to prioritize based on your methodology and your gut.
Overall, the OSWE was a tough but rewarding experience. It’ll make you sweat, and it gives you a solid foundation for tackling complex white-box pentests. I do recommend it.
Hey, I'd love to hear your thoughts! Just drop me an email.